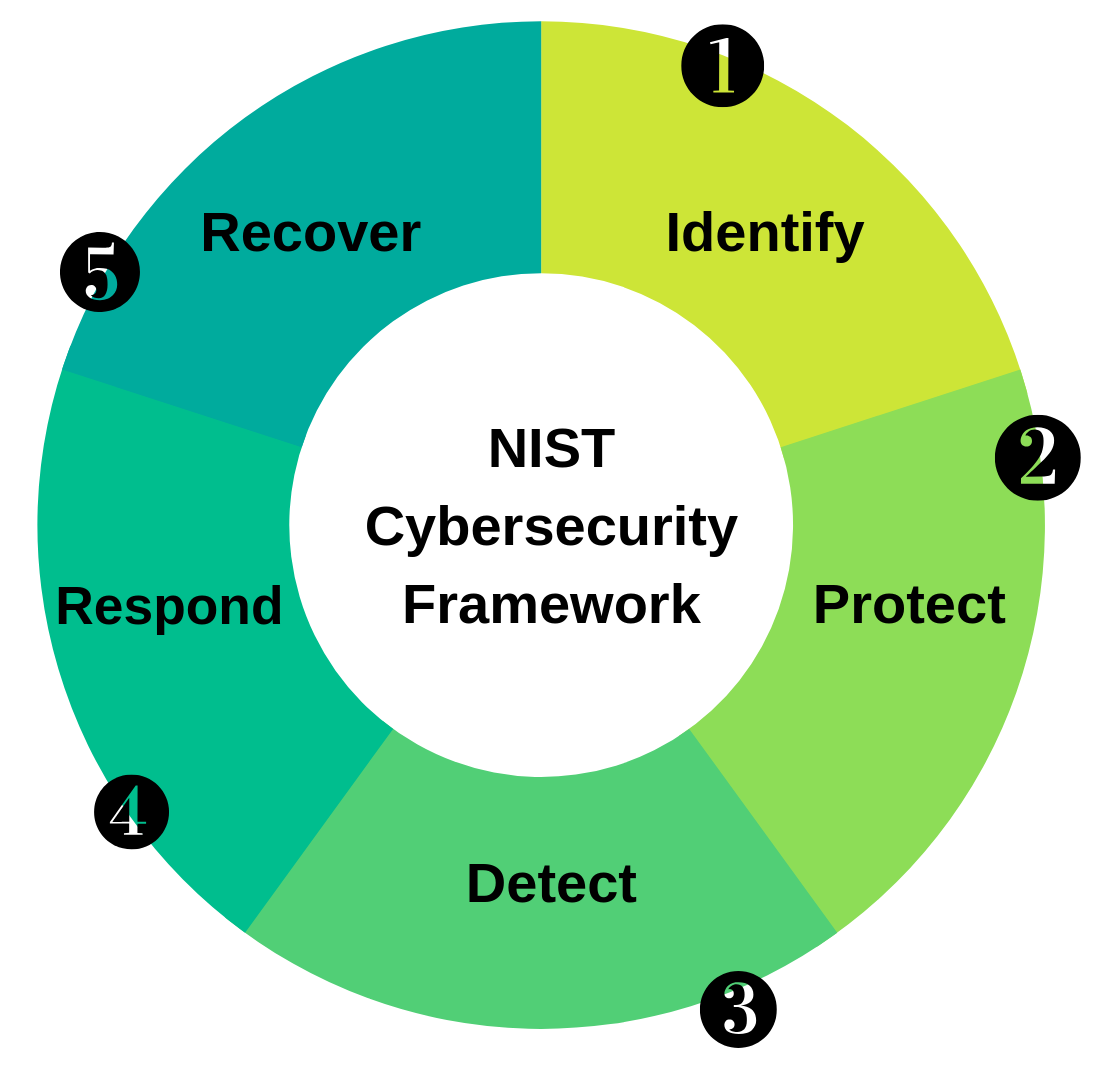
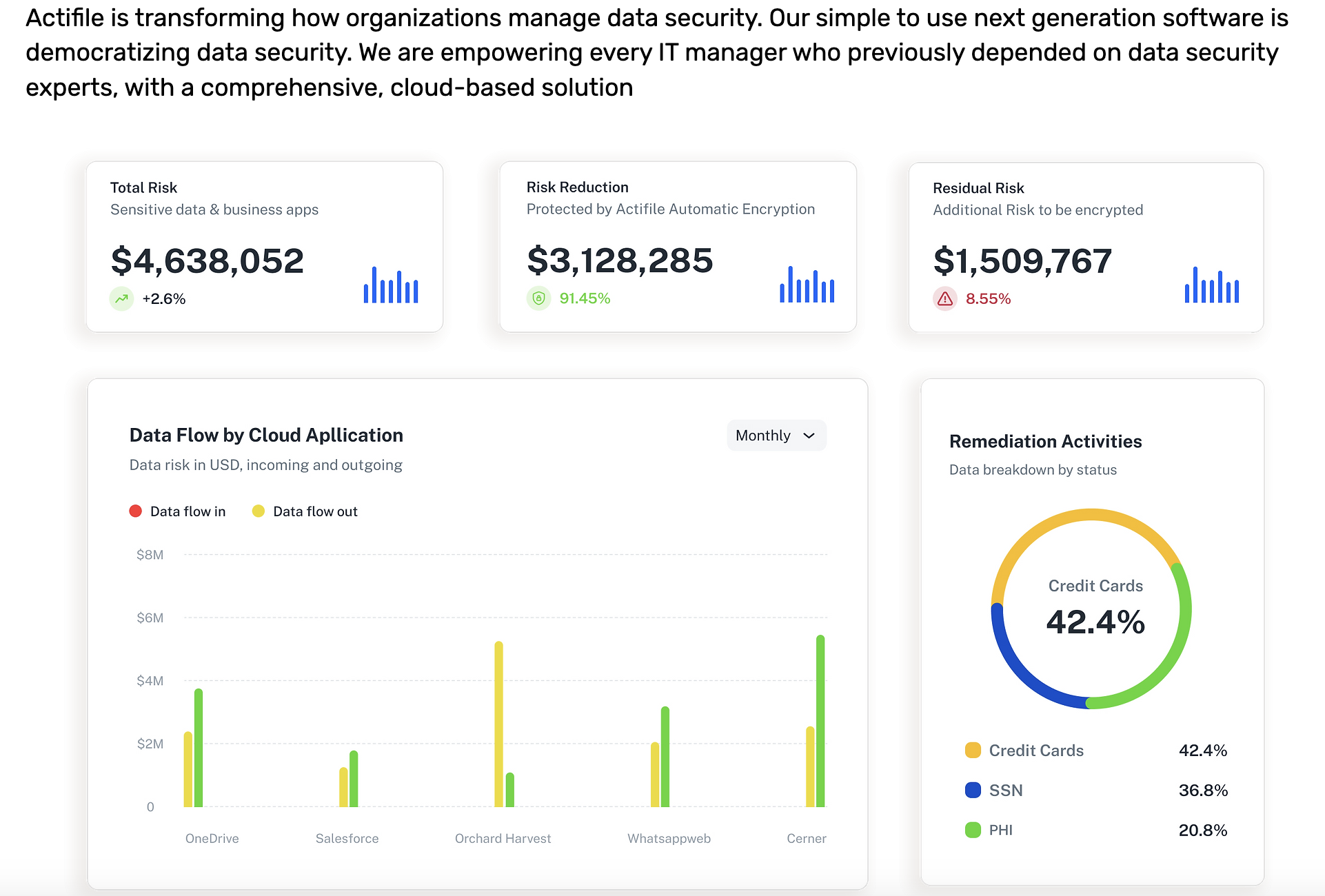
For many organizations, cybersecurity is often considered a “grudge expense”— an insurance policy against threats, breaches, and regulatory penalties. But in today’s hyper-connected, AI, digital-first world, cybersecurity is no longer just a...
James Oliverio
Recent Posts
Discover how to safeguard your business from hidden IT risks by mastering effective shadow IT management strategies.
Implementing Data Loss Prevention (DLP) solutions can safeguard your sensitive information, but the road to effective deployment is fraught with challenges.
In today's digital age, safeguarding sensitive information is more crucial than ever. Discover why Actifile stands out among other Data Loss Prevention (DLP) solutions.